3 things industrial control system enterprises should do to boost cyber-resilience
Here's an action plan for industrial control system cyber-resilience
 The increased connectivity and interoperability with IT/OT convergence via connecting OT systems, networks, and applications to enterprise IT amplifies the cybersecurity attack surface.
Image: Shutterstock
The increased connectivity and interoperability with IT/OT convergence via connecting OT systems, networks, and applications to enterprise IT amplifies the cybersecurity attack surface.
Image: Shutterstock
Enterprises in smart critical infrastructure-driven sectors such as manufacturing, energy, water, and transportation (among many others) rely upon the cyber-resilience of industrial control system (ICS) infrastructure to sustain business continuity. Business continuity here not only encompasses the feature of non-disruptive minimal service quality to customers but also the feature of ensuring the safety properties of that service. As Brian Deken, Business Development Manager of ICS giant Rockwell Automation, put it: "As a citizen, I'd like to know whether my drinking water is safe or whether a cyber-attack is affecting it or could possibly affect it". Imagine an event in a smart city with about a million people accessing maliciously targeted non-potable drinking water. How much could this event negatively affect society's economic, health, and lifestyle welfare? Is there a strategy by which the management in such enterprises can maintain business continuity in the event of inevitable cyber-attacks to mitigate these repercussions?
In this article, we provide a brief overview of how ICSs operate, their security challenges, and examples of cyber-attacks that have significant adverse repercussions on society. Subsequently, we provide a three-point action plan for ICS management to boost cyber resilience and maintain business continuity in the event of inevitable cyber-attacks.
An Overview of ICS Operation and its Security Challenges
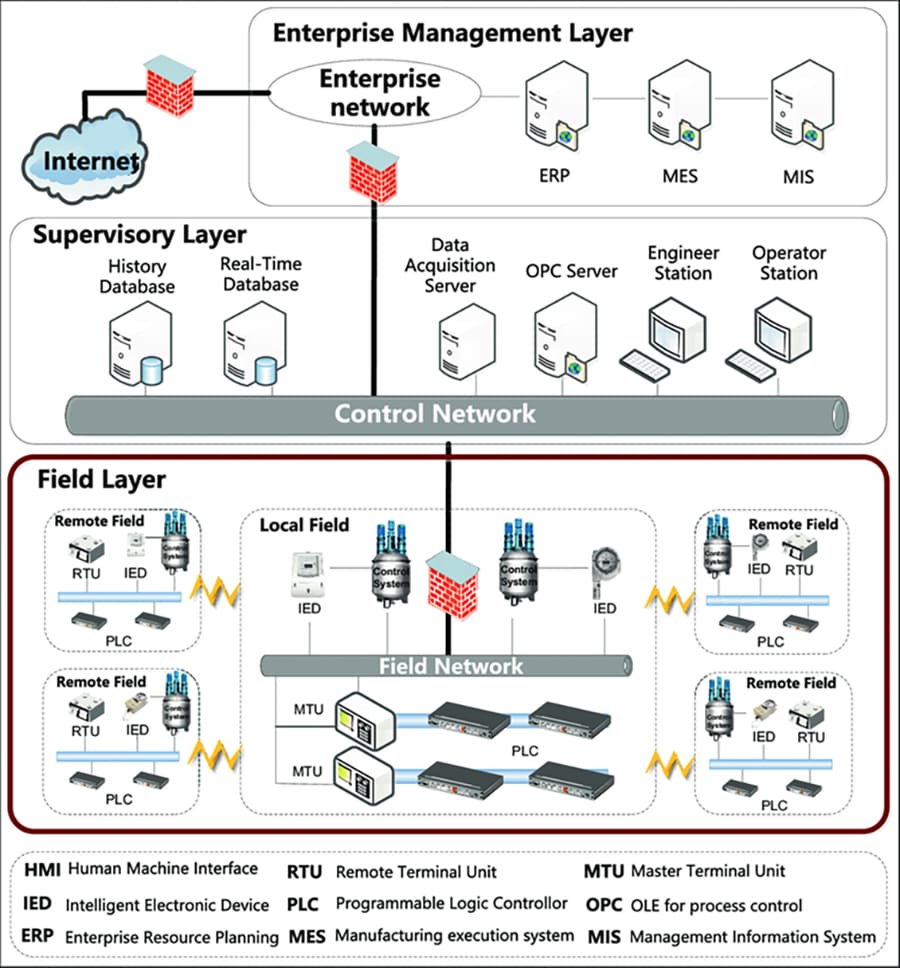
Smart critical infrastructure usually consists of operational technology (OT) devices, including legacy and proprietary mechanical gadgets (e.g., controllers, chillers, elevators) fitted with sensors and actuators. These are networked with each other via OT-specific wired or mobile/wireless technology (e.g., Modbus, CC-Link, and so on), where communication between interoperable gadgets takes place via custom software drivers. This OT network (e.g., spanning an industrial plant floor) is then managed via distributed and/or centralised IT and OT control using HMIs, application software, cloud computing, and human-driven dashboards. This popular IT/OT convergence in ICSs governs business process management in such systems.The increased connectivity and interoperability with IT/OT convergence via connecting OT systems, networks, and applications to enterprise IT amplifies the cybersecurity attack surface. In other words, the recent IT/OT convergence has minimised the traditional air gap between the IT and OT parts of an ICS enterprise that was the cornerstone of ICS cybersecurity. Legacy OT was designed and implemented before cybersecurity was even a concern in ICSs. Hence, the modern ICS in smart cities has a "patched-in" cybersecurity rather than the much-needed "baked-in" cybersecurity for their networks and applications. Consequently, this increases the risk of cyber-criminals accessing sensitive ICS data and making unauthorised changes to the ICS controls of industrial operations in critical infrastructure.
To drive home this point, according to Rockwell Automation, the number of cybersecurity incidents on ICSs between 2021 and 2022 alone is about one-third the number of similar incidents between 1980-2010. In addition, there has been a 50 percent rise in ransomware attacks on ICS in 2023 compared to 2022 (says Dragos, an ICS cybersecurity market leader). It is evident that the number of ICS cyber-incidents is rising exponentially by the year. Christopher Wray, the director of the US Federal Bureau of Investigation (FBI), says that in 2024, Beijing's efforts to plant offensive malware inside US critical infrastructure covertly were greater than ever before.
[This article has been published with permission from IIM Calcutta. www.iimcal.ac.in Views expressed are personal.]